PCAP Analysis of MySQL Data Extortion Attacks in HoneyShare
Exposed databases are a common target for Data Extortion attacks, yet many of these attacks rely on bluffs rather than actual data theft.
Using MySQL honeypots in HoneyShare, a set of extortion attacks was detected. In this post we analyse the PCAPs to find what the attacks actually do, we extract a bitcoin address, and other key data points.
The Attacks
The PCAP files capturing the attacks can be downloaded from the HoneyShare API:
honeyshare.Timeseries(attack_id).pcap(filename=f"capture.pcap")
Filtering for the MySQL protocol, here is one of the attacks in Wireshark:
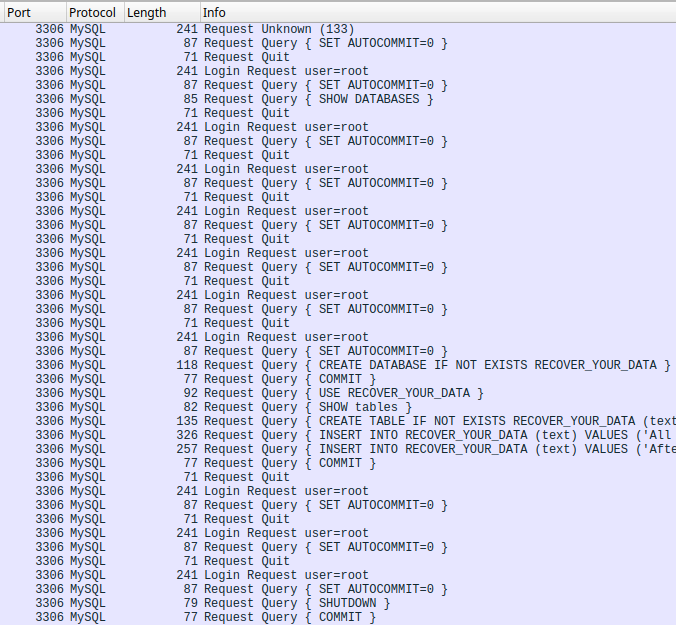
The honeypot contains a database with dummy data. Although the databases of the server are listed in the attack, no data seems to be extracted, even looking outside the MySQL protocol.
The interesting bit in the capture is the writing of the instruction for the ransom:
SET AUTOCOMMIT=0
CREATE DATABASE IF NOT EXISTS RECOVER_YOUR_DATA
COMMIT
USE RECOVER_YOUR_DATA
SHOW tables
CREATE TABLE IF NOT EXISTS RECOVER_YOUR_DATA (text VARCHAR(255))
INSERT INTO RECOVER_YOUR_DATA (text) VALUES ('All your data is backed up. You must pay 0.0075 BTC to bc1q998aen837juss7hs5jet3t96ghajgj67f5jg2q In 48 hours, your data will be publicly disclosed and deleted. (more information: go to hxxps://is.gd/yotuqu)')
INSERT INTO RECOVER_YOUR_DATA (text) VALUES ('After payment send mail to us: rambler+XXXXX@onionmail.org and we will provide a link for you to download your data. Your DBCODE is: XXXXX')
COMMIT
The attack does the following:
- Creates a database called
RECOVER_YOUR_DATA. - Creates a table called
RECOVER_YOUR_DATAwith a singlevarchar(255)column in said database. - Inserts messages with instructions for the ransom.
From this we get a bitcoin address, and a few other data points.
In the example attack the ransom is 0.0075 BTC. A ransom of 0.0074 BTC was also seen in other attacks. As of 2025-09-24, this would approx convert to 717.55 EUR and 844.75 USD.
Bitcoin Address, Emails and URL
This is the bitcoin address seen in every attack.
bc1q998aen837juss7hs5jet3t96ghajgj67f5jg2q
Looking at a blockchain explorer, as of 2025-09-24 there are two transactions, both from November 22, although none containing payments of 0.0075 BTC. The wallet is very likely used for other means.

The emails are onionmail.org and are the same with the exception of a code replaced here by XXXXX. The code is an alphanumeric string of length 5.
rambler+XXXXX@onionmail.org
There is a URL hxxps://is.gd/yotuqu, which is URL shortner. Itt eventually leads to a plaintext list of further instructions on how the user can exchange money to bitcoin, pay up and provide proof of payment. These instructions can be seen safely in this image.
Further Analysis
The attacks all originate from these IPs:
196.251.91.32
196.251.91.79
196.251.115.92
196.251.91.43
We can get some data out of HoneyShare API like so:
ipv4 = honeyshare.IPv4(ip)
ipv4.ipv4()
ipv4.hostnames()
Looking at an example output, we see basically the same for every IP:
{'IPv4': '196.251.91.32',
'CountryCode': 'NL',
'Hostname': '',
'LastSeen': '2025-09-24T08:00:28.344637Z'}
{'IPv4': '196.251.91.32',
'Hostnames': [{'Timestamp': '2025-08-31T15:18:12.610892Z', 'Hostname': ''},
{'Timestamp': '2025-08-01T17:57:29.073971Z', 'Hostname': ''},
{'Timestamp': '2025-07-06T20:59:51.171143Z', 'Hostname': ''},
{'Timestamp': '2025-06-12T13:58:26.127896Z', 'Hostname': ''},
{'Timestamp': '2025-04-21T16:13:03.517275Z', 'Hostname': ''}]}
The IPs have been detected by HoneyShare several times. But none ever reverse DNSed to a hostname. They are all geolocated to the Netherlands, which is likely where the attack is either being hosted or where the proxy for it is.
Looking into the history of the connections:
dates = set()
ports = set()
ipv4 = honeyshare.IPv4(ip)
for conn in ipv4.timeseries(pagesize=500)['Connections']:
dates.add(datetime.fromisoformat(conn['Timestamp']))
ports.add(conn['Port'])
min(dates)
ports
We see that the earliest connection dates back to March 12, and all connections target the default MySQL port.
2025-03-12 20:35:22
{'3306'}
Conclusion
With HoneyShare, we perform PCAP analysis to understand how a simple data extortion attack targets an exposed MySQL database. It's possible to see how the attacks seem to come from the same network, possibly a web host or proxy, and that they only connect to the default MySQL port 3306.
From the data we also obtained:
- A bitcoin address.
- A URL with instructions.
- Emails used in the attack.
It's seen these attacks don't actually fetch the data or encrypt it, and instead they just make empty threats hoping the victims will pay up out of fear of data leaks.
Learn more about HoneyShare, explore the API and library.